How to React to the Ledger Data Breach: 5 Recommendations
Published at – 6 min read – 1256 words
If you think you are amongst the users affected by the latest Ledger data breach, it is important not to panic! Follow a few simple steps and you can check the extent of the damage and keep an eye on the security of your account.
What are Data Breaches?
One of the unfortunate side effects of the modern, Internet-connected world is the data breach ― an uncontrolled leak of data and/or information. Very often is the case that you (the user) are not responsible for, or the cause of, such an intrusion. Companies have suffered (and will continue to suffer) embarrassing data breaches, whether it takes the form of server breaches, human error, or staff misconduct.
This information can range from usernames and passwords to tax IDs, physical addresses, and even payment details. These lists are then generally sold online to criminal groups who seek to use this information for profit.
Exploring the Ledger Data Breach
I have already written about the massive phishing campaign that has been going on since early September 2020. However, it was only a matter of time before the attackers sold the database with over 1,000,000 email addresses.
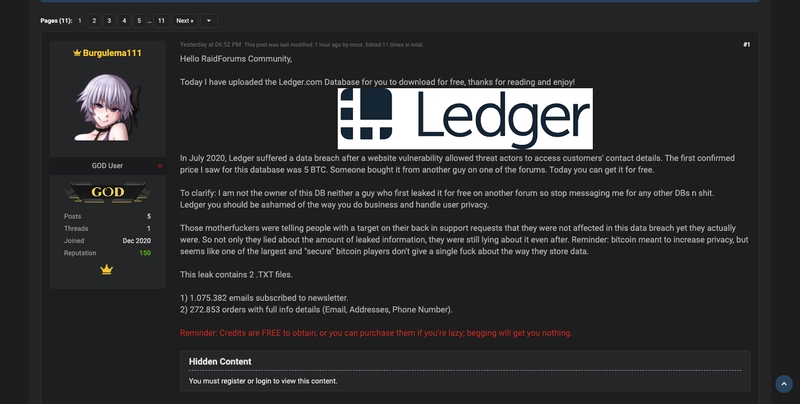
The database containing the personal information of over 270,000 Ledger customers has been posted on RaidForums, a marketplace for buying, selling, and sharing information stolen from computer systems. It appears that the buying and selling is actually the result of a purchase on another forum by user Burgulema111.
The data leak includes two parts:
- The database containing the emails, personal addresses, and phone numbers of Ledger hardware wallet buyers (most likely obtained from a Shopify interface); and
- A list of over 1 million emails from Ledger’s marketing campaign.
Syntax of the DB file:
[email]| [name_surname]| [address]| [city]| [state]| [mobile_phone]
Recommendations to follow
Below, I recommend 5 (+1) actions to take after such a large data breach:
1. Don’t Send Your Seed!
Whenever you are asked (especially in an unsolicited manner), do not reveal or send your seed to ANYONE. NEVER SEND YOUR SEED! Even if you think it is the CEO of Ledger himself: DO. NOT. DO. IT. A seed is a collection of 24 random words needed to retrieve the private key to your wallet. Revealing or sending this to anyone is analogous to telling someone the combination to your online safe.
Your funds are NEVER in danger if you follow common sense, which is to NEVER send or reveal your seed! Ignore emails that come to you about a detected, urgent security issue or an unverified account. If your email is on the list, consider it compromised.
2. Check What Personal Data They Have Stolen
Through Have I Been Pwned and IntelX, you should be able to search for your personal email address. This allows you to check whether or not, in addition to your email address, your personal address or your cell phone number has also been stolen.
By checking stolen personal information, you should be able to keep track of how much of your personal information has been disclosed and take subsequent countermeasures.
3. Consider Changing Your Email address and/or Phone
Once your email address is online, you will get lots of emails. Lists, such as Ledger’s, are recycled by spammers and attackers to create massive spam and phishing marketing campaigns. You should consider that email account compromised and, resultantly, you should open emails you receive very carefully! Even if it seems to you that the recipient may be trusted.
If you find that your primary email address is in the database, it is a good idea to change email accounts. While you might think that simply abandoning your old, compromised email address and updating your social accounts to the new email address that you have created would help, you might want to think twice. There is the risk that email providers can delete the email account and then there could eventually be an account takeover. So, do not completely abandon your old email address when changing the email address of your social accounts to your new email. While we are on the topic, it would make sense to change your password(s).
To change your cell phone, the procedure is a bit more complex. You could opt to buy a new data SIM and use it for your main accounts (bank, insurance, etc.). Another approach would be to change your mobile number, but there could be risks associated with this. In the first days, since the operation takes time and if you mess up, you risk finding your account blocked, because they often send a recovery SMS to your old number. In the future there is risk, because it is possible that the previously used mobile number will be recycled and assigned to another person.
Ultimately, be suspicious of any calls and emails you receive. After data breaches, phishing activity often occurs as criminals hope to take advantage of consumer fear and confusion.
4. Constantly Monitor Accounts
While you may think you are “immune” to these threats, closely monitor all of your email, social, and banking accounts. Attackers often use social engineering to steal your identity in addition to sending phishing campaigns. Warn acquaintances and colleagues who may be receiving calls on your behalf and be sure to make them aware that they should not trust the individual(s) reaching out to them.
You should monitor any changes to your medical and insurance accounts. In addition, it is important to keep an eye on your financial and credit accounts. Identity thieves may have enough sensitive information to use your existing accounts or create new ones in your name.
If you think that your data has been used for crimes, report it immediately to federal, state, or local law enforcement!
5. Never pay ransoms or anything else!
If you ever receive an email that threatens you and subsequently asks for a ransom, never pay them. If you think you are in danger and fear for your physical safety, please contact your local authorities right away.
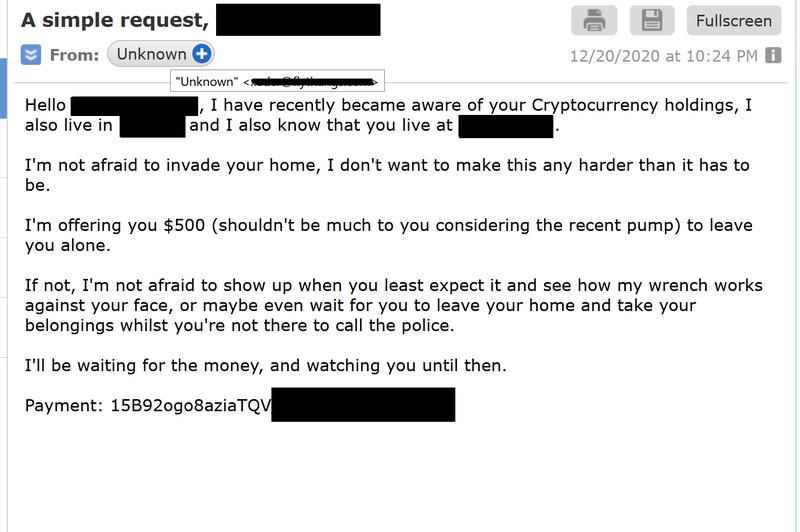
6. Prevent it from happening to you again!
This current situation is truly alarming and it should be used as a lesson and a warning for the future. Undoubtedly, there will be many people asking themselves, “How can I prevent this from happening again?” It is important to remember that while the company is to blame for this leak, it can also highlight a growing problem with regard to privacy protections. That is: How can you prevent this type of information (email address, home address, and cell phone) from getting into the wrong hands?
It is of the utmost importance that before doing simple things like making an online purchase or signing up for a social platform, that you read the tedious and bureaucratic Privacy Policy and Terms of Service. This way, you will be able to understand what data is collected and for what purpose it is used. If these disclosures are missing, it would already be a red flag.
I’m not affiliated with Ledger and I’m not taking any parts of the company. I just wanted to write the paragraph to wonder you how much information someone collects.
Let me know what you think, contact me now!
Some statistical information
Table of email domains found in the data breach:
| Domain | Number of occurrences found |
|---|---|
| gmail.com | 587.545 |
| yahoo.com | 62.630 |
| outlook.com | 14.794 |
| protonmail.com | 13.120 |
| yandex.ru | 4.865 |
| tutanota.com | 634 |
| … | … |
Major states present:
| States | Number of occurrences found |
|---|---|
| United States | 91.442 |
| Germany | 23.519 |
| United Kingdom | 21.130 |
| France | 17.263 |
| Canada | 12.730 |
| Italy | 5.672 |
| Russia | 4.953 |
| Denmark | 1.670 |

