What is Stealth Address technology and Why Does Monero Use It?
Published at – 6 min read – 1218 words

Monero Stealth Address
Monero is based on the CryptoNote protocol and utilizes the most powerful cryptographic techniques in an effort to protect the privacy of the sender, recipient, and obfuscate the amount transacted.
To protect the sender’s privacy, Ring Signatures has been implemented to prevent transaction inputs from being distinguishable from one another. Ring Confidential Transactions (RingCT), which hides transaction amounts, was implemented in block #1220516 during January 2017 and since September 2017, this feature became mandatory for all transactions on the Monero network. In addition to these two key cryptographic techniques that Monero utilizes to ensure the privacy of every Monero user during the transaction process, Stealth Addresses ensure the privacy of the recipient. This article will focus on how Stealth Addresses work, why they were introduced, and discuss some details not commonly known about this essential feature of Monero.
Let’s imagine that you have to buy a product on an e-commerce platform from a merchant. The payment system will return a public address, so that the payment can be sent to the merchant. In the case where you use a transparent blockchain, such as Bitcoin or Ethereum, the link between your address and the address of the merchant is obvious. So, on transparent blockchains, a third-party from outside of the transaction has the potential to track how and where your funds are spent.

Bitcoin Transparent Ledger
Thanks to Ring Signatures and RingCT, your privacy as the sender is protected and the transaction amount is unknown. To further prevent any potential transaction analysis and, more importantly, to ensure the privacy of the recipient (or, simply put, how and where you spend your funds), Monero uses Stealth Addresses.

Hidden connection between Stealth Address and Wallet
A Stealth Address is an automatically generated, one-time public key (otherwise known as a random, one-time address) that is created by the sender, on behalf of the recipient, when a transaction on the Monero network is initiated ― think of this as a “burning address”. This one-time public key is recorded as part of each transaction and designates who can spend an output in a future transaction. While observing the blockchain, third parties (such as a government or a company that performs in-depth transaction analysis) are not able to link your wallet address and the merchant’s wallet address; therefore, it is not possible to tell if Monero is being sent from you to the merchant.
Through the use of Stealth Addresses, when you send Monero to a merchant, the output received by the merchant is not publicly associated with the merchant’s wallet address. If you are in a position where you need proof that you sent Monero to the merchant, your wallet will be able to verify that the transaction was indeed sent. In addition, Stealth Addresses ensure that the merchant can always know that a third-party will not be able to see if or when any Monero has been sent and received. This unique feature of a Monero transaction is especially attractive to merchants, because it serves as a way to protect sensitive financial and operational information.
To better understand the concept of Stealth Addresses, let’s consider an example where you send a parcel to your friend via the postal system ― where every movement of the parcel, from sender to recipient, is tracked. At the beginning of this exchange, your friend tells you the home address. From there, you bring the parcel to the post office and send it along to your friend’s home address that was provided. During the course of this transfer, via the tracking code that was provided by the postal system, you can see the movement of the parcel between you and your friend, including your friend’s home addresses. This is analogous to Bitcoin ― where every movement of the transaction, from sender to recipient, is traceable. However, if you told your friend to use a temporary post box, no one would associate the movement of the parcel to your friend, since finding the owner of a temporary box is difficult.
How are these one-time addresses generated? Your Monero wallet’s public address is a 95-character string, which incorporates two public keys (public view key and public send key) that are mathematically derived from your seed. When a customer sends Monero to a merchant, the customer will use the public keys in the merchant’s address along with some random data to generate a unique one-time public key for the merchant’s new output. While observers of the blockchain can see the one-time public key, the customer and the merchant are the only parties who definitively know that, in fact, the customer sent the Monero to the merchant.
While the merchant’s wallet is scanning or syncing, the wallet’s private view key is being used to check all transactions and accompanying outputs on the blockchain in an effort to locate the output destined for its wallet. Once the output is detected and received by the merchant’s wallet, the merchant is now able to calculate a one-time private key that corresponds with the one-time public key and, if the merchant chooses, spend the relevant output with the wallet’s private spend key. Thanks to Stealth Addresses, this transaction process occurs without publicly linking any transaction to the merchant’s wallet address.

One stealth address and one payment
Simply put, a Stealth Address is a powerful cryptographic technique that prevents outputs from being linked to a recipient’s public address. As described above, this is accomplished through the use of one-time public keys. Only the recipient has the ability to identify their designated output while scanning the blockchain and, once received, the output can only be spent by the recipient. Seeing that outputs are unlinkable, the recipient’s privacy is secured.
While the concept of Stealth Addresses can seem quite technical to some, one of the user-friendly features of this technology is that the sender and recipient do not need to take any further steps outside the normal process of performing a transaction, because Stealth Addresses are implemented by default. Despite being a key feature of a Monero transaction, and through being implemented by default, Stealth Addresses can fly under the radar and be considered just another cog in the well-oiled machine.
A commonly asked question is: “But if they’re randomly generated, is it possible a collision could occur?” Luigi1111, collaborator and member of the Monero Core Team, gives us an estimate. Using the birthday paradox for the calculation, it would take about 2^126 Stealth Addresses generated to have a 50% collision occur. You would need 85,070,591,730,234,615,865,843,651,857,942,052,864 transactions, when at the time of writing, the transactions within the Monero network are approximately 8 million. For comparison, there are far fewer grains of sand in the world than the number of transactions that would be needed for such a collision. This is an impressive number that confirms the security of this powerful cryptographic technique.
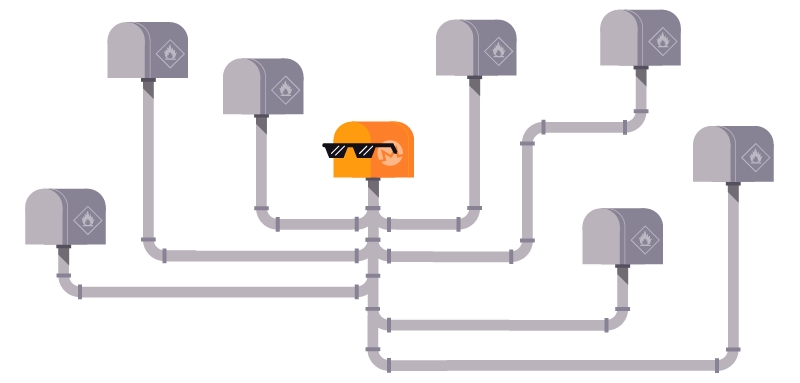
Many stealth addresses are linked to wallet
Lastly, an important point to make is what Stealth Addresses are not. With payment systems that accept Bitcoin or Ethereum, you might find a different payment address that is generated randomly. This is not a Stealth Address, because at the blockchain level, analysis and tracking tools would be able to find a link between the two different addresses, along with what these addresses have received and sent.