All Articles - Page 2
Started to be written in 2017, SerHack Blog represents a solid but unique point of view in Computer Science field. From cryptocurrencies to information security, from reverse engineering to phishing: many topics are depicted using layman terms. What are you waiting for? Read one of any articles.

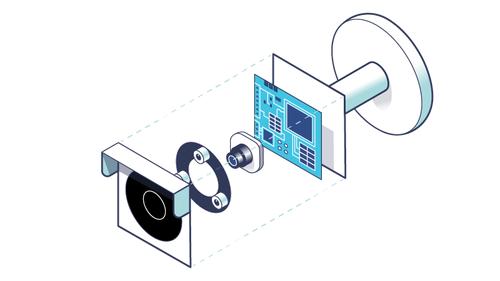
Dissecting Reolink RLC-810A Hardware: A Detailed View
– Now that we know how device booting works, let’s try to extract some parts from the firmware that we downloaded in Part 1 of our series. Here, we are interested in two main sections: the Linux kernel (which takes care of booting the device services) and the flattened device tree (which allows … See Full Article
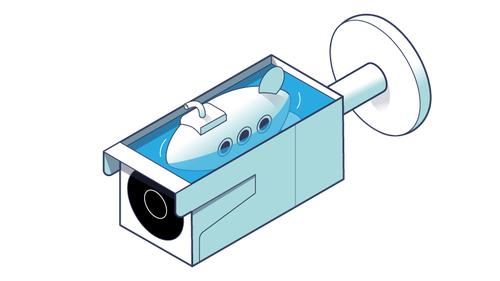
Booting an Embedded OS: the Booting and U-Boot Phase
– In the first post, we introduced embedded devices and started to scour through and extract information from Reolink IP camera firmware. At the end of the post, we ran Binwalk, which showed various types of files such as Flattened Device Tree, uImage Header, and UBI File System. For the second … See Full Article
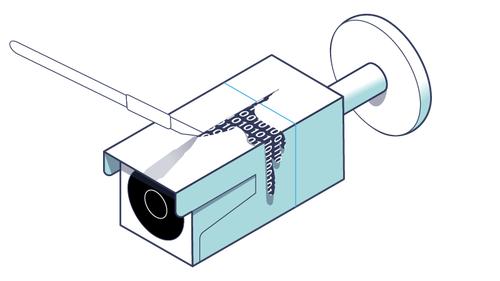
Introduction to Firmware Analysis of a Reolink IP Camera
– Embedded devices continue to increase in popularity and one category, in particular, that has become en vogue as of late is the Internet of Things (IoT). The emergence of these next generation technologies has driven the home automation evolution from simple light bulbs to cloud-connected printers, … See Full Article
The Story Behind the Alternative Genesis Block of Bitcoin
– In this article, I attempt to explain the early source code of Bitcoin and make correlations with the source code currently in use. My intent is to help you better understand the early details regarding the history of Bitcoin and the enigmatic figure of Satoshi Nakamoto. As far as newcomers to … See Full Article
Unveiling the Anonymous Author: Stylometry Techniques
– One of the techniques that fascinates me most about writing is textual analysis, which includes semantics (the meaning of words) and syntax (the use of signs and letters to construct sentences). Throughout history, both classical and modern, there are numerous examples of authors who wanted to keep … See Full Article