All Articles - Page 5
Started to be written in 2017, SerHack Blog represents a solid but unique point of view in Computer Science field. From cryptocurrencies to information security, from reverse engineering to phishing: many topics are depicted using layman terms. What are you waiting for? Read one of any articles.

Monitoring Your Own Infrastructure Using Grafana, InfluxDB, and CollectD
– For some companies, infrastructure is the heart of its business. Specifically, I am referring to those companies which need to manage data and applications located on more than one server. It is essential for a company to monitor its infrastructure nodes, especially if the company does not have … See Full Article
The Myth of Privacy and End-to-End Encryption in Zoom
– Zoom is a service to host meetings without the need to install and configure complicated applications: it is one of the many solutions for those who, during quarantine, want to keep in touch with friends and relatives. In this last period of lockdown, Zoom is becoming popular because of how simple … See Full Article
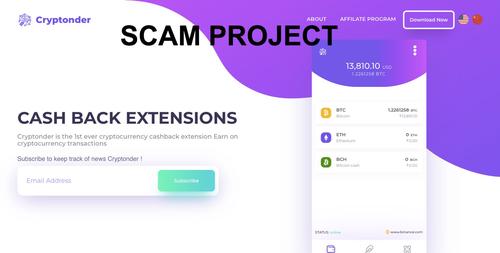
Take off the Infrastructure of a Scammer: Cryptonder and Torowallet
– On a rainy autumn day, I was contacted like many users by a suspicious individual on Telegram. He insisted on asking for the help of the user who had to recover his wallet which contained several bitcoins. Our “friend”, hencereferred as “M.”, insisted that the user has to … See Full Article
Monero Windows and Linux CLI Compromised: The Analysis of Binaries
– As mentioned in the getmonero.org blog post, the binaries of Command Line Interface (CLI) of Monero were recently compromised. For readers who are unaware of Monero, it is a cryptocurrency which aims to protect the financial privacy of its users. It is based on well-known technologies such as ring … See Full Article
Introducing the New Website: From WordPress to Gohugo
– At the beginning, I started my website on 14th May of 2017 when the recent Wannacry malware has appeared. My first post, in fact, was to discuss and to analyze the malware in deeper, explaining technical concepts to people who do not know anything about Windows and SMB. In my life, I meet some … See Full Article