Posts tagged on Security
How to React to the Ledger Data Breach: 5 Recommendations
– If you think you are amongst the users affected by the latest Ledger data breach, it is important not to panic! Follow a few simple steps and you can check the extent of the damage and keep an eye on the security of your account. What are Data Breaches? One of the unfortunate side effects of the modern, Internet-connected world is the data breach ― an uncontrolled leak of data and/or information. See Full Article
A Practical Analysis of the Ledger Phishing Email
– Attempts at phishing and social engineering attacks have increased exponentially as of late, especially towards users who are active in the cryptocurrency space. Recently, there has been much discussion about a cunning attempt by phishers against Ledger and its users. In this article, we’ll dissect: How Ledger devices secure your Bitcoin and other cryptocurrencies What makes it, and other … See Full Article
Phishing: Persuading People through a Voice Synthesized by AI - Part 1
– I get between 10 to 20 emails per day and, usually, more than half of them are phishing attempts. Phishing attempts are a type of email scam that typically aims to obtain personal data of the victim, including username and password for email accounts and popular services (Gmail, Hotmail, mail.ru, Twitter, Amazon, etc.), through pages forged ad hoc to simulate login sections. “Your account … See Full Article
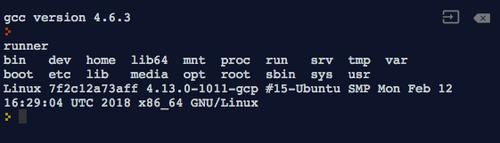
Monero Windows and Linux CLI Compromised: The Analysis of Binaries
– As mentioned in the getmonero.org blog post, the binaries of Command Line Interface (CLI) of Monero were recently compromised. For readers who are unaware of Monero, it is a cryptocurrency which aims to protect the financial privacy of its users. It is based on well-known technologies such as ring signatures and Confidential Transactions; I suggest reading Mastering Monero to better understand its … See Full Article
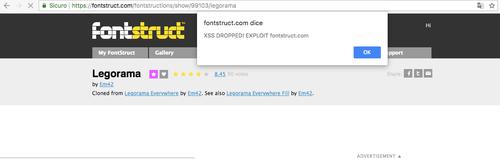
FontStruct - Break the Font InfraSTRUCTure!
– The website FontStruct allows even novice users to create their own personal font from scratch. A very simplified procedure: you sign up and you are ready to compose your font. Everything is offered through a simple interface as a free service. Not bad for a free service! Unfortunately, the developer who set up this service has not thought very well about security, repeatedly implementing … See Full Article
MEGA Chrome Extension Hacked - Detailed Timeline of Events
– TLDR; On 4 September at 14:30 UTC, an unknown attacker managed to hack into MEGA’s Google Chrome web store account and upload a malicious version 3.39.4 of an extension to the web store, according to a blog post published by the company. Upon installation or auto-update, the malicious extension asked for elevated permissions to access personal information, allowing it to steal login/register … See Full Article
Hackers Can Take Full Control of Online Compilers through a Common Exploit
– Online compilers are a handy tool to save time and resources for coders, and are freely available for a variety of programming languages. They are useful for learning a new language and developing simple programs, such as the ubiquitous “Hello World” exercise. I often use online compilers when I am out, so that I don’t have to worry about locating and downloading all of the resources myself. Since … See Full Article
Introduction to MoneroV and its Inherent Risks
– The “MoneroV” coin is an impending unofficial fork of the Monero blockchain with many “red flag” characteristics that have alarmed the Monero community. Many users are wondering: could the MoneroV fork be a scam project? This article discusses risks for individuals claiming MoneroV, and describes how MoneroV opens an attack vector on the overall privacy of the Monero network itself. Types of … See Full Article
How to Crash the iPhone with a Single Telugu Character
– In recent years, Apple has been heavily criticized for the security implications of their market centralization and policy of irreversible operating system updates. Mobile device users are strongly pressured to install packaged iOS upgrades that cannot be rolled back. While this practice greatly increases security for most users, there is an inherent danger to this centralization. Every flaw or … See Full Article
How I broke Envato Search Engine
– How Envato managed two critical vulnerabilities discovered by me TLDR; Envato devs had not developed a strong filter in order to avoid any XSS Attack, and I noticed that I could perform a XSS Injection. I have contacted Envato and, after some investigations, they have discovered that my vulnerabilities were critical! They thanked me and patched the vulnerabilities within 5 business days. Good job … See Full Article