All Articles - Page 7
Started to be written in 2017, SerHack Blog represents a solid but unique point of view in Computer Science field. From cryptocurrencies to information security, from reverse engineering to phishing: many topics are depicted using layman terms. What are you waiting for? Read one of any articles.

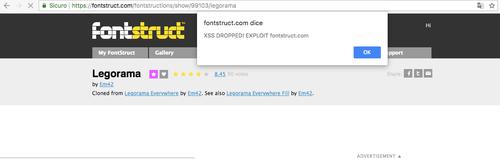
FontStruct - Break the Font InfraSTRUCTure!
– The website FontStruct allows even novice users to create their own personal font from scratch. A very simplified procedure: you sign up and you are ready to compose your font. Everything is offered through a simple interface as a free service. Not bad for a free service! Unfortunately, the … See Full Article
MEGA Chrome Extension Hacked - Detailed Timeline of Events
– TLDR; On 4 September at 14:30 UTC, an unknown attacker managed to hack into MEGA’s Google Chrome web store account and upload a malicious version 3.39.4 of an extension to the web store, according to a blog post published by the company. Upon installation or auto-update, the malicious … See Full Article
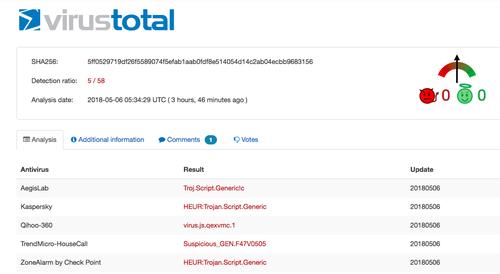
Deobfuscation and Understanding a Trojan Jscript
– Over 50% of cyber attacks are executed through malware, whose job is to find a flaw to inject other types of viruses including malware, adware and much more. Knowing the computer remotely, it can spy on the screen and even crypt the files: a wrong click and you lose anything. It is estimated that … See Full Article
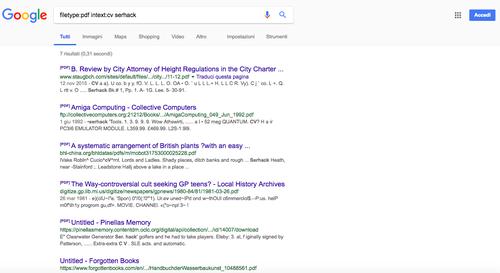
Google Dorks: The Powerup for the Search Engine
– It is estimated that Google has downloaded more pages than any other search engine in the field. With over billions of pages and a relatively low execution time, the popular Californian search engine is able to satisfy all research, both for educational purposes and for purely curiosity purposes. … See Full Article
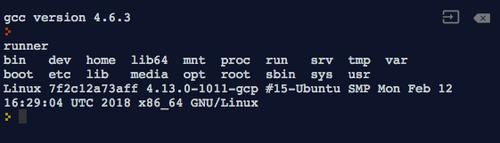
Hackers Can Take Full Control of Online Compilers through a Common Exploit
– Online compilers are a handy tool to save time and resources for coders, and are freely available for a variety of programming languages. They are useful for learning a new language and developing simple programs, such as the ubiquitous “Hello World” exercise. I often use online compilers when I am … See Full Article